Cyberattacks are becoming increasingly sophisticated, targeting organizations of all sizes. One essential aspect of a robust cybersecurity strategy that is often overlooked is log management. By collecting, analyzing, and managing logs effectively, organizations can identify potential threats, respond to incidents swiftly, and ensure compliance with regulatory requirements. Here’s why log management is vital in strengthening cybersecurity and how it serves as a cornerstone of effective defense strategies.
Understanding Log Management and Its Role
Log management involves the collection, storage, and analysis of log files generated by various systems, applications, and devices within a network. These log files record events, transactions, and activities, providing a detailed trail of all operations. Logs can include user access records, application errors, system updates, and network activity.
By analyzing these logs, security teams gain insight into the behavior of their systems and users. This information is invaluable for identifying suspicious activity, detecting potential vulnerabilities, and preventing cyberattacks. Effective log management serves as an early warning system, alerting organizations to irregularities before they escalate into significant breaches.
Detecting Security Incidents and Threats
One of the primary benefits of log management is its ability to detect security incidents in real time. Logs provide visibility into network activity, making it possible to identify anomalies such as unauthorized access, unusual data transfers, or repeated login failures.
These irregularities often indicate potential cyber threats, including malware infections, phishing attempts, or brute-force attacks. Advanced tools for real-time log analysis enable security teams to respond quickly to emerging threats. Organizations can identify patterns that indicate malicious activity by monitoring logs continuously and correlating data from multiple sources. This proactive approach minimizes the window of opportunity for attackers and reduces the potential damage caused by security breaches.
Supporting Incident Response and Forensics
When a cyberattack occurs, log management plays a crucial role in incident response and forensic investigations. Logs serve as a record of what happened before, during, and after an incident, providing the evidence needed to understand the scope and impact of the attack.
Analyzing logs helps security teams trace the origin of the attack, identify compromised systems, and determine how the attackers gained access. This information is critical for developing effective mitigation strategies and preventing future incidents. Furthermore, logs provide a detailed timeline of events, enabling organizations to meet regulatory and legal requirements for incident reporting.
Ensuring Compliance With Regulations
Compliance with industry regulations and standards is a top priority for businesses, particularly in sectors like finance, healthcare, and retail. Many regulations, including GDPR, HIPAA, and PCI DSS, require organizations to maintain detailed logs of system activity and ensure data integrity.
Log management systems simplify compliance by automating the collection and storage of logs in a secure and organized manner. These systems also generate reports that demonstrate adherence to regulatory requirements, making audits more straightforward and reducing the risk of non-compliance penalties.
Enhancing Network Visibility and Performance
Effective log management improves not only security but also overall network performance. By analyzing logs, organizations can identify bottlenecks, misconfigurations, or system failures that affect operations. This insight allows IT teams to optimize network performance, enhance user experience, and maintain business continuity.
Logs also help organizations track resource usage, such as bandwidth or storage capacity. This information is vital for planning infrastructure upgrades, scaling resources, and ensuring that systems remain efficient and reliable.
Overcoming Challenges in Log Management
While log management offers significant benefits, implementing an effective system comes with challenges. The sheer volume of logs generated by modern networks can be overwhelming, making it difficult to store and analyze data efficiently. And, identifying meaningful patterns within large datasets requires advanced analytics and expertise.
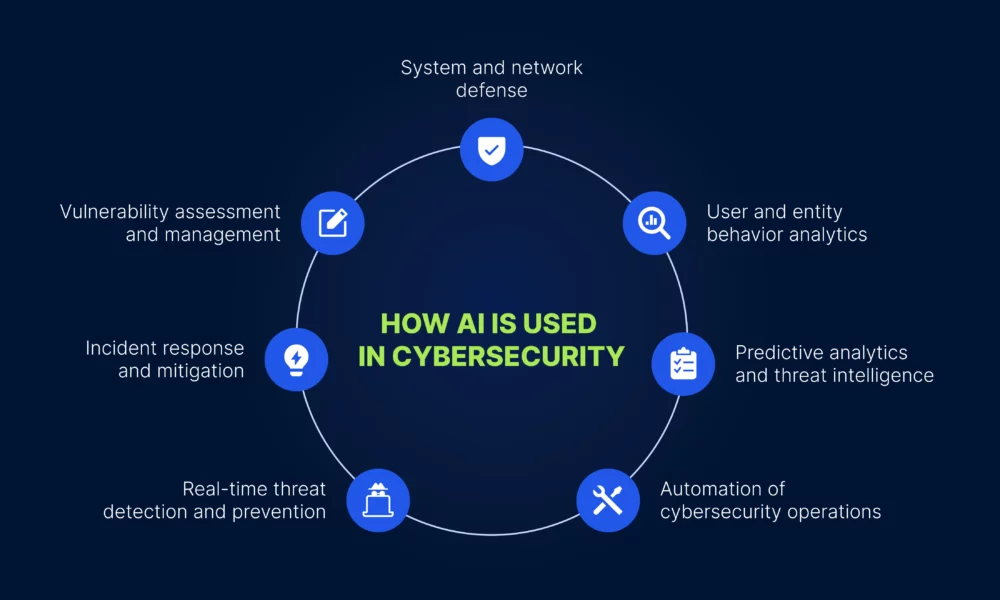
To address these challenges, organizations can leverage centralized log management systems that aggregate data from multiple sources into a unified platform. These systems use machine learning and artificial intelligence to automate analysis, identify anomalies, and generate actionable insights. By adopting these technologies, organizations can overcome the complexity of log management and focus on strategic cybersecurity initiatives.
Integrating Log Management With Security Tools
Log management should be integrated with other cybersecurity tools and practices to maximize the effectiveness of log management. Combining log management with intrusion detection systems (IDS), firewalls, and endpoint protection enhances visibility and strengthens defenses.
For example, integrating logs from different systems allows for correlation analysis, where data from various sources is combined to detect patterns that might not be evident in isolated logs. This holistic view of network activity improves threat detection and response capabilities, enabling organizations to act swiftly and decisively in the face of cyber threats.
In an era where cyber threats are continually evolving, log management is no longer optional—it’s a necessity. By providing real-time insights, supporting incident response, and ensuring compliance, log management lays the foundation for a resilient cybersecurity strategy. Organizations that prioritize log management not only reduce their risk of breaches but also gain a competitive edge by demonstrating their commitment to data security.
As cyberattacks grow more sophisticated, investing in robust log management systems and leveraging advanced tools for log analysis ensures that your organization stays one step ahead of potential threats. With the right systems and practices in place, log management becomes a powerful ally in the ongoing fight against cybercrime.














Leave a Reply